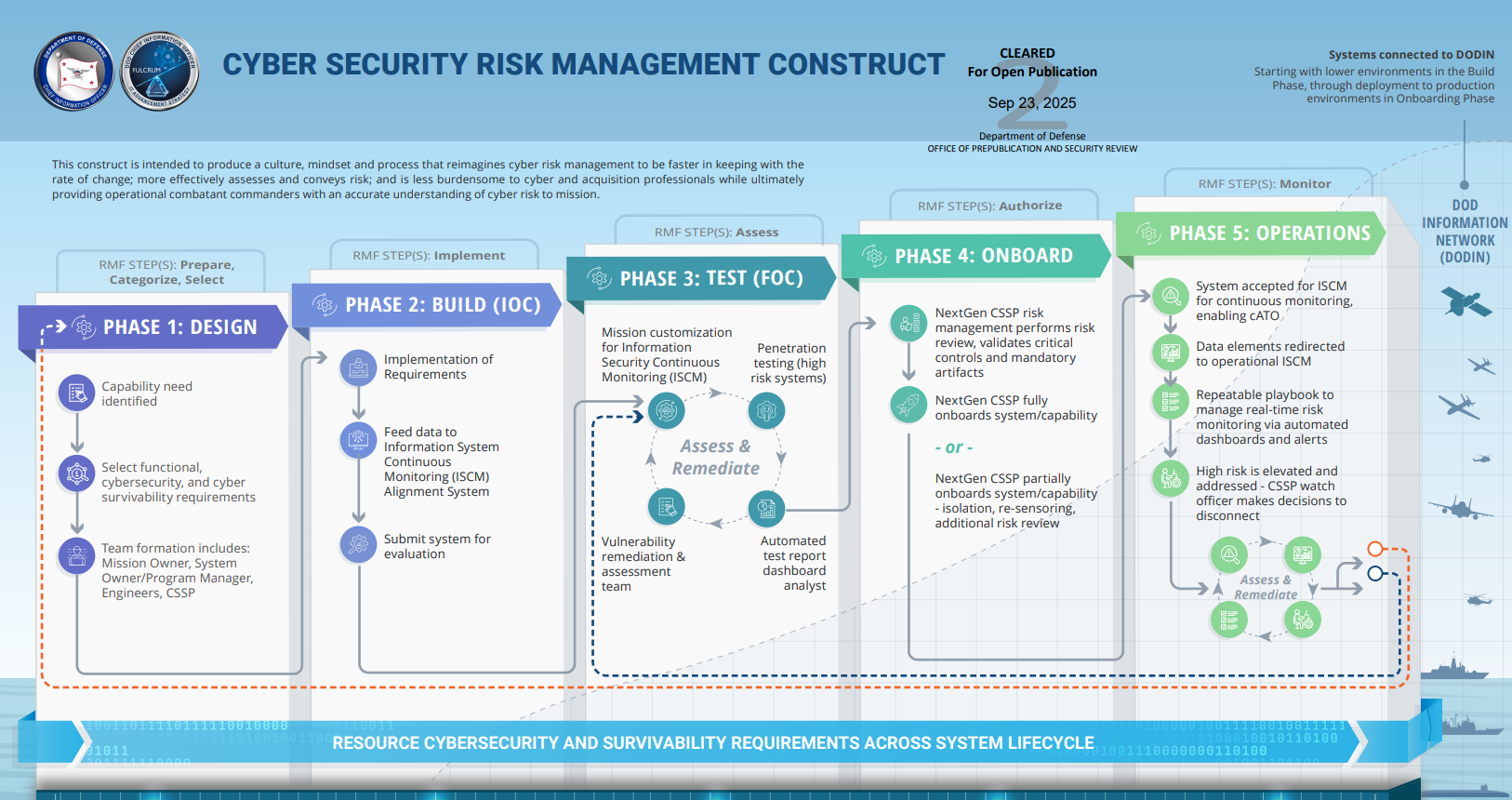
An Overview of the Department of War's New Cybersecurity Risk Management Construct (CSRMC)
The United States Department of War (DoW) has announced a significant evolution in its cybersecurity posture with the introduction of its new Cybersecurity Risk Management Construct (CSRMC). This framework is not a mere rebranding of the existing National Institute of Standards and Technology (NIST) Risk Management Framework (RMF), but a fundamental departure from the static, manual processes that were ill-suited for modern, dynamic IT environments.
The CSRMC serves as a direct, strategic response to the limitations of the legacy RMF, which was overly reliant on time-consuming, checklist-based assessments. This blog post breaks down the foundational tenets — continuous monitoring, DevSecOps, and automation — and next steps for federal mission owners.
Tackling Current ATO Challenges
The new CSRMC is a direct, long-overdue overhaul of how the RMF has been implemented in the modern era, rather than an abandonment of its foundational principles.
For years, the federal government relied on RMF, but its implementation became characterized by a legacy process that was cumbersome, outdated, and ill-suited for modern realities like agile software development, rapid cloud adoption, and the increasing integration of artificial intelligence (AI). The traditional RMF process, centered on obtaining an authority to operate (ATO), is a rigorous, time-consuming assessment that takes, on average, 4-18 months to navigate. It is heavily reliant on manual, document-based reviews, creating a significant administrative burden and a bureaucratic bottleneck. (We talk about these challenges and how documentation automation is the key to compliance modernization in our recent blog post, “Why Federal GRC Needs an Engineering Mindset.”)
The most critical limitation of this legacy process is its snapshot-in-time view of a system's security posture. In an era of rapidly advancing threats, a three-year-long ATO means continuous oversight is not guaranteed, leaving a gap where new vulnerabilities and compliance drift can arise undetected. This static nature slows the delivery of secure capabilities and leaves defense systems vulnerable.
The CSRMC is the DoW's direct answer to these problems. It is essentially the institutionalization of modern governance, risk, and compliance (GRC) engineering principles. By formally listing automation, continuous monitoring, and DevSecOps as foundational tenets, the CSRMC signals a mandatory shift in mindset. It is not a total rejection of NIST guidance, but an organizational and strategic move to enforce what was previously treated as an optional best practice.
This new construct transitions the military's approach from a compliance-centric document drill to a mission-driven, continuous, code-driven risk practice, designed to provide real-time cyber defense at the speed of relevance. The ultimate goal is to enable modern concepts like continuous authority to operate (cATO) and zero trust architecture (ZTA).
Continuous Monitoring: The Core of CSRMC
Defined as the ongoing, automated process of assessing and analyzing an organization's security posture, continuous monitoring (CM) is designed to detect vulnerabilities, misconfigurations, and emerging threats in a near-real-time manner. This provides ongoing awareness and real-time situational awareness necessary to make informed, risk-based decisions.
The strategic importance of CM becomes clear when it is paired with the concept of cATO. Whereas a traditional ATO provides a static, one-time approval for a set period, cATO is a dynamic security approach that enables ongoing authorization. This model allows an organization to continuously assess and deploy subsystems that meet its risk tolerances, effectively moving away from a point-in-time assessment approach. The CSRMC explicitly merges these two concepts into a single operational goal with its foundational tenet of continuous monitoring and ATO, which enables a constant ATO posture.
The transition to cATO offers a compelling value proposition that addresses the core shortcomings of the legacy process. By shifting from periodic assessments to automated, real-time compliance checks, cATO reduces the time and cost associated with ATO renewals and streamlines the process. The benefits include an improved security posture, lower risk, increased transparency, and the ability to deliver new capabilities to the user with greater agility.
This shift, however, is not a simple technical upgrade. It is a fundamental change management initiative that requires a holistic approach encompassing people, processes, and technology. The traditional ATO process, by its very nature, fostered a siloed, "gatekeeper" mentality where security was viewed as a final, bureaucratic hurdle. For cATO to succeed, the organizational culture must transform into one of shared responsibility and continuous collaboration. This is precisely why the CSRMC lists DevSecOps as a foundational tenet and a core competency required for cATO. The framework is designed to break down these silos and integrate security into the daily work of development and operations teams, making the security process a seamless part of the digital transformation journey.
GRC Engineering: The Operational Blueprint for CSRMC
CSRMC is, at its core, the direct call for GRC engineering. This is a profound shift that transforms GRC from being a manual, reactive, and documentation-heavy function into a proactive, continuous, and integrated engineering discipline.
Traditionally, RMF implementation treated compliance as a periodic, bureaucratic gate. This siloed approach created a gap between development speed and security verification. GRC engineering directly closes this gap by embracing the principles of automation and DevSecOps that the CSRMC now officially enshrines as foundational tenets.
How the CSRMC Enables GRC Engineering
The CSRMC operationalizes GRC Engineering by requiring the integration of risk and compliance activities directly into daily engineering workflows:
Compliance as Code: Instead of relying on human-generated documentation, GRC engineering turns regulatory and security requirements into executable code. This Policy-as-Code is integrated into continuous integration/continuous deployment (CI/CD) pipelines, ensuring that security controls are deployed and verified automatically, making compliance a byproduct of normal development.
Continuous Assurance: The CSRMC mandates continuous monitoring, which is the chief practice of GRC engineering. This enables teams to measure control effectiveness in real-time, moving beyond the static, snapshot-in-time assessment of the past. If a configuration drifts from its secure baseline, tools immediately detect and often automatically remediate the issue, maintaining a compliant posture without manual intervention.
cATO Enablement: The ultimate measure of success for both the CSRMC and GRC engineering is the shift to cATO. GRC engineering provides the constant, auditable stream of real-time risk data necessary to sustain an ongoing authorization. This allows organizations to securely deploy capabilities at the speed of mission requirements because the compliance evidence is continuously generated by the system itself, rather than collected and reviewed manually.
By incorporating GRC engineering principles, the CSRMC is forcing the cultural and procedural changes necessary to manage cybersecurity risk with the same agility and precision used to manage software development. The goal is to move from checkbox compliance to engineered assurance.
DevSecOps and the Secure Software Factory
The shift to a continuous security posture, as mandated by the CSRMC, cannot be achieved without a new operational model: DevSecOps. Listed as a foundational tenet by CSRMC, DevSecOps integrates security into every stage of the software development lifecycle (SDLC), fostering a culture of secure by design. By embedding security from the outset during the CSRMC's design phase, this proactive stance reduces the number and severity of vulnerabilities that could manifest later.
Automation in the CI/CD pipeline is the critical enabler of this approach. Each code change triggers a series of automated security tests, providing immediate feedback to developers. This includes scans such as static application security testing (SAST) to detect code vulnerabilities early, software composition analysis (SCA) to identify vulnerabilities in third-party dependencies, container scanning mechanisms to find vulnerabilities within your container images, secrets detection to prevent hardcoded credentials, and Policy-as-Code to limit baseline configuration findings. This continuous stream of data on security and compliance is the direct input for the continuous monitoring process, allowing teams to address vulnerabilities promptly and maintain the pace of development without compromising security.
The ultimate operational model for a cATO-enabled environment is the secure software factory. This factory is a collection of people, tools, and processes that leverages automation and standardized toolchains to continuously deliver secure software. The CSRMC's focus on this model reflects a profound change in philosophy. The traditional RMF model allowed for manual, ad-hoc changes to systems in production, which often led to configuration drift and a divergence from the original security baseline. This approach eliminates configuration drift, makes continuous monitoring vastly more reliable, and is a direct precursor to achieving cATO.
The success of this new model is predicated not just on technology, but on a cultural shift. The greatest barriers to DevSecOps adoption are often cultural resistance and the tool overload that can overwhelm teams. This is why the CSRMC emphasizes a leadership-driven, collaborative approach that promotes a security-first mindset.
Enabling Zero Trust Architecture
The CSRMC is a critical stepping stone toward achieving a ZTA. Zero trust is a security strategy, not a product, based on the core principles of never trust, always verify, and least privilege access. It assumes a hostile environment and operates on the premise that threats can come from both inside and outside the traditional network perimeter.
The CSRMC's foundational tenets are perfectly aligned to enable the implementation of ZTA. The two frameworks are mutually reinforcing and work together to create a more secure environment. The CSRMC, therefore, serves as the DoW's practical, mission-specific implementation plan for the broader federal zero trust strategy laid out by the Office of Management and Budget (OMB) and the Cybersecurity and Infrastructure Security Agency (CISA). It is not just aligned with ZTA; it is the operational prerequisite for its successful implementation, providing the technical capabilities and enforcement mechanisms required for a zero trust policy to be effective.
Overcoming the Hurdles
The shift to a continuous, code-driven security posture is a necessary evolution, but it is not without significant hurdles. The history of large-scale organizational transformations indicates that success is rarely a straight line forward, and the process can be a long and difficult journey. The CSRMC, while elegant in its design, will face predictable challenges in its implementation.
Chief among these is the human factor. The success of the framework is predicated on a profound cultural shift — one that moves from a reactive, checklist-based mentality to a proactive, security-first mindset. This requires leadership-driven initiatives, a willingness to break down long-standing organizational silos, and a commitment to fostering a culture of collaboration between development, security, and operations teams. Furthermore, the technical expertise required for this transition can be a major challenge. Teams may lack the necessary skills for advanced automation and integrating new tools. This can be particularly difficult for smaller organizations with limited resources.
The process of integrating new technologies with existing legacy systems can also be a complex and time-consuming technical roadblock. This is often compounded by tool overload, where an organization attempts to integrate too many disparate tools, leading to fragmented practices and complicated workflows.
To overcome these challenges, a strategic, iterative approach is essential. A realistic, actionable roadmap for success should include the following recommendations:
Strategic Planning: Begin with an honest and accurate assessment of your agency’s current capabilities and readiness for change. Define a clear modernization roadmap that prioritizes high-impact use cases and balances risk aversion with the imperative for innovation.
People and Culture: Invest in robust training and upskilling initiatives to address technical skill gaps. Secure strong leadership buy-in and promote a culture of shared responsibility and open communication to break down organizational silos.
Technology and Automation: Consolidate and standardize toolchains to reduce complexity and streamline workflows. Leverage a solid foundation of pre-built, secure services, such as the Defense Information Systems Agency (DISA) Cloud Infrastructure-as-Code (IaC) baselines, to accelerate the transition and provide inheritable controls.
The success of the CSRMC will ultimately depend on the leadership's ability to translate this strategic mandate into decentralized, team-level changes, providing the resources, training, and cultural support needed to overcome the inertia of legacy processes.
Conclusion
The Department of War's Cybersecurity Risk Management Construct represents a necessary and timely evolution in the approach to securing mission-critical systems. It moves beyond the limitations of the traditional RMF, which is unable to keep pace with the speed of modern threats and the agility of agile software development. By institutionalizing continuous monitoring, DevSecOps, and automation as foundational tenets, the CSRMC provides the operational blueprint for achieving a continuous security posture.
The transition to a cATO model, enabled by the CSRMC's principles, transforms cybersecurity from a periodic compliance burden into a continuous, mission-enabling capability. Furthermore, the framework's direct alignment with zero trust principles ensures that the specific implementation efforts are a cohesive part of the broader federal cybersecurity strategy. This strategic investment in a resilient, code-driven, and continuously defended cyber environment is essential for ensuring that U.S. warfighters maintain technological superiority against rapidly evolving adversaries and for safeguarding national security in every domain. The CSRMC is more than just a new framework; it is a blueprint for a more resilient future.
If you are interested in learning more about how Aquia can help your agency in its compliance modernization initiatives, contact us at federal@aquia.us.